We recently hosted a breakfast seminar on handling data breaches and wider crisis response management in Guernsey. Having worked on a number of incidents with clients and lived through the experience ourselves, we wanted to organise the breakfast seminar as a way of highlighting the importance of the issue and to consider practical, strategic approaches to managing incidents.
Partners Richard Field and Richard Sheldon analyse the results from the polls, which were run on the day, and summarise some of the core themes and takeaways from the session.
Background
Data security is one of the core risks that all businesses must consider. High profile data breaches hit the headlines on a daily basis, many involving household names. We all hope it won't happen to us, but the reality is that we are likely encounter some form of breach or security incident at some point.
Companies are increasingly being judged by their initial responses, both by a nervous customer base and sceptical media, long before regulators reach decisions as to any potential sanctions that might be imposed.
We have come a long way as a jurisdiction in recent years. Since the States announced its intention to implement GDPR-equivalent legislation in Guernsey in 2016, the community has worked tirelessly to not only review and revise its collective approach to data security, but to raise awareness of the various threats that exist.
Poll 1
In the last 12 months at board level have you discussed either a data breach within your organisation or the risks of a data breach?

A reassuringly high level of positive responses. Having been involved in the States Industry Working Group on data protection, it is clear that the new data protection legislation and the conversations around its impact have helped bring information security higher up the corporate agenda. The number of those who were uncertain may reflect that not all attendees sit at board level, but it does also imply that those organisations would benefit from greater transparency in terms of policy and strategic approach. Information security is after all a collective responsibility at all levels within the business.
WhiIst discussions at board level are a great starting point, implementation and monitoring are also key to successfully mitigating risks.
Poll 2
Does your organisation have a data breach response plan?
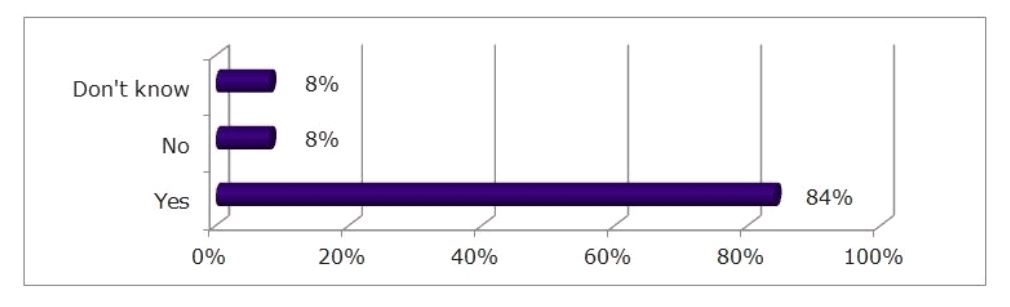
The difference in these response levels suggests that not all of the discussions at board level have translated into concrete action. As outlined in the session, having a plan in place is better than having no plan at all, regardless of the size and severity of the incident. Assessing the risks, defining the team and processes and stress testing the policies and procedures are all fundamental to minimising the impact of a data breach or cyber security incident.
Core Themes
1. Failing to prepare is preparing to fail
- Make sure your organisation has a response plan to deal with data breaches and similar incidents. The plan should be rehearsed periodically, updated as required and hard copies kept securely in core locations. Make sure staff are aware of it and their role in implementing it.
- Map your data estate so that you know what data is held and where, who is able to access it and what is being done with it – it will make assessing the impact of any incident much easier to determine.
- Consider insurance – the fine print of any policy wording is crucial, but being protected can minimise the financial impact.
- Review not only your information security arrangements, but those of your supply chain and intermediaries. Consider what contractual protections you have in place.
2. Name your team and have a bench
- Know who to talk to from all relevant areas of the business. Make sure they are briefed on what is expected of them and you have rehearsed how an incident might play out.
- Include a "substitute" for each function, in case of illness, absence or similar.
- Have a list of trusted and experienced advisers (legal, tech, PR & communications) on call in case of an emergency.
3. Incidents come in many shapes and sizes - be flexible
- Not all situations will require escalation to management or indeed externally, but all incidents nonetheless need to be recorded.
- Establish the facts, consider a proportionate response and assess what steps need to be taken to protect your position.
4. The first 72 hours
- Establish the facts and take steps to contain the incident. Gather and preserve evidence to help deal with the incident, but also to inform any regulatory investigation or assist with any subsequent legal proceedings.
- Consider whether you have an obligation to report the breach to the Data Protection Commissioner (or similar authority in another jurisdiction) and whether there is an obligation to notify affected data subjects.
- Deal with individuals in an ethical manner – you may not have an obligation to notify them, but it may be the right thing to do.
5. Technical focus
- Whilst it is vital to "keep the lights on" and aim to restore business as usual, the priority is normally to stop the attack or fallout from the incident.
- Engage with external forensic teams where necessary in order to determine the facts and decide on a response strategy.
- Preserve evidence of technical aspects of the breach for future use; consider chain of custody and privilege surrounding investigations.
6. Consistent lines of communication
- Develop your communications scenario plans in advance.
- Understand your audiences – colleagues, clients and the media.
- Develop a set of key messaging that is agreed across all levels of the incident response team and senior management for communication with your audiences; determine which communication channels you will use to reach each of your audiences.
- Invest the time in open and honest communication with colleagues.
- Ensure that your client communications are delivered via a trusted source and that your colleagues can respond with confidence to client queries. Put yourself in their shoes and think about what they would want to know and how to reassure them in order to maintain/rebuild trust.
- Stay in control of your messaging – you may not be able to control what the media does with it, but you can control how much and what you say.
7. The Regulator's expectations
- Demonstrate that you are managing the incident, implementing existing response plans and are aware of the various implications of the situation.
- Consider your legal obligations and demonstrate that you are working to fulfil them.
- Engage with the regulator and do not be afraid to ask questions and work collaboratively – those who are actively working towards compliance will be treated differently to those who are ignoring or wilfully breaching their obligations.
8. Learning
- Make sure that any learning points are considered, disseminated around your team/organisation and included in a revised breach response plan.
Conclusions
Data is the new oil; its significance and value cannot be overestimated. Securing that data is a core aspect of good governance and something that customers and clients have come to expect. Incidents could be a consequence of a variety of internal or external factors, but having a plan in place to deal with them is inevitably going to reduce the impact on your business.
Building trust in a digital age is vitally important, so managing your communications and how you handle an incident are key elements to achieving that goal.
Whilst the principles outlined above were considered in the context of a data breach scenario, many are equally valid and applicable to other crisis situations. Don't forget to take that moment to step back, take a breath and assess what has happened, it could make all the difference.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.


