This decision is interesting for readers involved in IT security and mobile communications. The board of appeal had to assess a new access method that preserves computer security, but at the same time increases the convenience of authorized users when using their elec¬tronic devices.
Here are the practical takeaways from the decision T 0277/16 (Location-based computer access/GOOGLE) of 26.6.2018 of Technical Board of Appeal 3.5.06:
Key takeaways
Increasing the convenience of authorized users when using their elec¬tronic devices, and thus providing a new access method balancing user convenience and security considerations is not merely a non-technical policy.
A non-intrusive and seamless way of changing device behavior, based on its physical location and its user-dependent actual access history, is intimately tied to the use and usability of the device for the legitimate user and therefore contributes to the technical character of the invention as a whole.
The invention
This European patent application concerns a location-based access control system that balances computer security and user convenience.
The core idea was to designate certain physical locations as familiar (e.g. the user's home or work place) and to require less complex and less burdensome security rules in familiar areas than in other areas. For example, a shorter passcode might be required inside the familiar area, so that logging in in a familiar place is less intrusive for the user than elsewhere.
The invention further provides an automatic way of designating the familiar area. It is proposed to monitor the successful login events and, essentially, to accept every location as familiar where the user has successfully logged in a minimum number of times. The system records the GPS location or the network address for every successful login attempt, groups them into logins at the "same" location and then classifies every such group with a minimal number of logins as part of the familiar area.
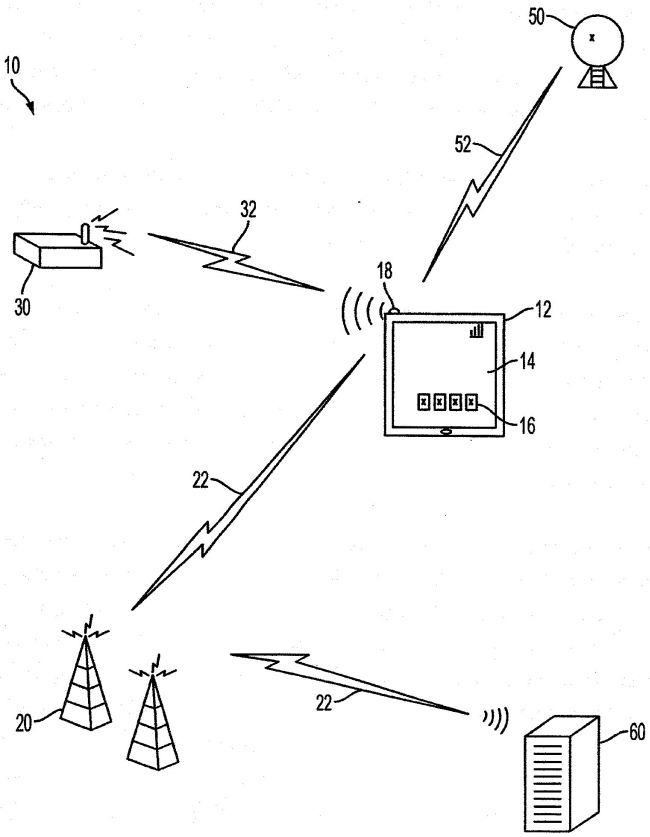
Fig. 1 of EP 2 629 228
Here is how the invention was defined in claim 1:
Claim 1 (main request)
A method, comprising:receiving, via an input of a portable electronic device (12), a request to access the electronic device (12);
the electronic device (12) implementing a first security rule requiring a first authentication process when the electronic device (12) is physically located in a familiar area and a different second security rule requiring a different second authentication process when the electronic device (12) is located outside of the familiar area[,] the second authentication process being more complex for the user or requiring more time for the user than the first authentication process; and;
receiving, via an input of the portable electronic device (12), a plurality of successful user authentication entries,
characterized in that the method further comprises:
determining a location of the device (12) corresponding to each of the successful user authentication entries,
wherein determining the location of the device (12) comprises one or more of:
receiving global positioning system data (52) and determining the location based on the global positioning system data (52), and
receiving a network address corresponding to a wireless communications network (22, 32) that the device (12) has detected, and determining the location based on the network address;
saving, in a computer-readable memory, data representative of each of the entries and each entry's corresponding location; and
automatically designating, by a processor without a requirement for user entry of location information, the familiar area for the electronic device (12),
wherein designating the familiar area comprises designating the familiar area based on the data representative of each of the entries and each entry's corresponding location, and
wherein designating the familiar area comprises:
determining a set of successful user authentication entries that were received during a time period,
grouping the entries from the set into a plurality of location-dependent subgroups,
determining a size of the set and a size of each subgroup,
identifying each subgroup having a size that at least equals a size threshold, wherein the size threshold corresponds to a portion of the set size, and
for each subgroup having a size that at least equals the size threshold, classifying the location for that subgroup's entries as the familiar area.
Is it patentable?
The first-instance examining division had refused the application for lack of inventive step.
On appeal, the board first addressed the examining division's line of argumentation, and did not share the division's view that the claimed invention was obvious over D1. Interestingly, the board implicitly accepted the problem of automatically determining a familiar area depending on usage patterns, e.g. based on successful logins, as a technical problem:
In the decision under appeal, the examining division assessed inventive step starting from D1, found that the claimed invention differed from D1 in that a familiar area was automatically determined and how, and thus considered the objective technical problem to be solved by the claimed invention as being "how to define a familiar zone [...] automatically [...]" (see points 7.2 to 7.3 of the reasons).
However, D1 discloses that zones are user-defined and does not suggest that it could be otherwise (specifi¬cally, the first full sentence of page 2, right column, does not say that security zones are only "typically user-defined" but that they are "user-defined" and that typical ones are e.g. "home", "work" and "airport").
The zones in D1 are predefined according to policy deci¬sions in view of "security concerns" (see para¬graph 2). For instance, a company might or might not decide that an employee's home is safe (or, at least, safer than a "public place") and that, consequently, the employee should profit from more lenient login require¬ments at home than in a hotel room or an airport. These zones are meant to be fixed – although some flexibility will have to be provided to account for developments such as users moving house or changing their preferred hotels.
In contrast, the familiar area as claimed may change over time according to a learning process and its extent does not depend on the security of the locations involved. For instance, the user's preferred coffee shop might, according to the invention, become a "familiar area" over time even though it is a public place with little security.
This is not to say that the invention ignores security considerations entirely. The authentication requirements in a new location are only relaxed once it can be assumed, in view of repeated successful authentication "entries", that the user is actually authorized, and the electronic device has not been stolen. This is, however, a different security concern than that addressed in D1.
Therefore, the skilled person addressing the problem of automatically determining the zones of D1 would not, without exercising inventive activity, consider the claimed manner of automatically determining a familiar area depending on usage patterns, let alone based on successful logins.
The board is also unaware of an objective technical problem which would naturally arise in the context of D1 and which the skilled person would solve, without exercising inventive activity, by providing the claimed solution.
Accordingly, the board did not follow the examining division's arguments and in fact considered another prior art document, D3, to be the closest prior art:
D3 discloses (see references above) that a portable electronic device may require different authentication processes in view of typical usage patterns, "learned" from actual usage, at authorized locations measured e.g. via GPS, and wherein the authentication process may be less complex or require less time for the user at "familiar locations"; see paragraph 85).
D3 also discloses that authorized locations – which correspond to the "familiar" area in the sense of the claims – are typically defined by radial distance around the device location detected in learn mode, for instance around a fixed GPS location or an access point (see paragraphs 47, 48 and 60), and that there may be several authorized locations per user and device, i.e. that the "familiar" area may extend over several physical locations (see e.g. paragraph 80).
The board acknowledged that claim 1 differed from D3 in that the familiar area is learned from – and may vary with – the frequency and proximity of "successful user authentication entries" at clusters (groups) of measured GPS locations or detected network access points.
The board considers that this feature increases the convenience of authorized users when using their elec¬tronic devices, and thus provides a new access method balancing user convenience and security considerations.
This is substantially the same difference that the examining division found to exist over D1 and consi¬dered to be a straightforward implementation of a "non-technical policy" (see the decision under appeal, points 7.3 and 7.4 of the reasons). Implicitly, this argument was applying the so-called COMVIK approach based, in particular, on T 641/00, headnotes I and II.
On the one hand, the board agreed that the difference implements a "policy", but it disagreed with the examining division that it was a non-tech¬nical policy which does not contribute to inventive step:
The invention provides a non-intrusive and seamless way of changing device behavior, based on its physical location and its user-dependent actual access history. The distinguishing features are thus intimately tied to the use and usability of the device for the legitimate user and therefore contribute to the technical character of the invention as a whole (see T 641/00, headnote I). In particular, the distinguishing features address the very real technical problem of preventing device access should it be stolen and taken to a location where the legitimate user has never authenticated him/herself to the device. The board judges, accordingly, that achieving the effect of the distinguishing features cannot be treated as an aim to be achieved in a non-technical field which, according to T 641/00, headnote II, may legitimately appear in the formulation of the objective technical problem.
Returning to D3, and in view of the fact that D3, too, discloses access methods balancing user convenience and security considerations, the objective technical problem solved by the invention over D3 may be considered as providing an alternative computer access method striking such a balance. However, in the board's view, D3 does not suggest the criteria according to which the familiar area is determined by the distinguishing features depending on user-dependent actual device usage (see point 9.3 above).
Accordingly, claim 1 was found to involve an inventive step over D3. Since no other prior art on file provided for a different view, the board set aside the decision under appeal and remitted the case to the examining division to grant a patent.
More information
You can read the whole decision here: T 0277/16 (Location-based computer access/GOOGLE) of 26.6.2018
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.

