Businesses have been scrambling since Friday evening when news spread that a ransomware attack named WannaCry is compromising organizations at an alarming rate. In less than 48 hours, it has compromised more than 130,000 organizations worldwide in over 150 countries. Early investigative reports have suggested that this particular malware was among the tools held by the National Security Agency (NSA) employed to exploit system vulnerabilities in Windows which were leaked by WikiLeaks, for which Microsoft had released a patch for over two months ago. Experts expect additional attacks to occur due to residual system infections, copy-cat viruses or the release of additional malware arising from the NSA leaks. The recent attack could have been prevented by an update Microsoft previously made available to Windows users.
Despite warnings and update reminders, businesses frequently fail to implement available updates needed to protect their systems and data from new threats. Hackers know this fact and thus have launched the first of what is expected to be numerous attacks arising from the now publicized NSA tools. If nothing else, this recent event again brings home the critical importance of updating software and security systems in a timely manner. Given the seriousness of this hack, Microsoft has also released emergency patches for older, off-support versions of Windows. For any organization running Windows, it is critical that they ensure all applicable patches have been installed. The original patch and the emergency patches can be found at: http://www.catalog.update.microsoft.com/Search.aspx?q=KB4012598.
Many Windows servers and workstations still remain vulnerable and organizations must continue to apply the latest security patches. However, more compromises are expected with the start of the workweek.
Ransomware Persists as a Legitimate and Viable Threat
Even though some security experts predicted that ransomware attacks would recede this year, that is not happening and the NSA leak suggests there will be additional attacks. Entities such as multinational corporations, hospitals, or energy companies are attractive targets for ransomware due to the ability to infect multiple computers on a single network and encrypt valuable data. Moreover, up-dating system software and security programs can be more complex and costly for such entities given their sheer size, thus, exposing them to significant attacks based upon the vulnerability of their systems.
Ransomware is a form of malicious software that infiltrates computer systems or networks, encrypting data until the victim pays a ransom, which is frequently demanded in untraceable Bitcoin. The average ransom demanded in 2016 rose from $294 to $1,077 dollars.1 Most ransomware is generally spread when a user clicks on a malicious attachment in an e-mail or on a hyperlink. Two of the more significant ransomware threats in 2016 ("Locky" and "Cerber") were spread via massive email campaigns. However, in this latest attack, the ransomware has been more successful through self-propagation, i.e., by gaining entry into businesses and automatically seeking out and infecting other vulnerable machines.
Preventative Measures to Mitigate Risk of a Ransomware Attack
Companies often fail to address the risk of ransomware until they are already the victim of an attack. However, by adopting a proactive rather than reactive strategy, and investing in a few key defensive practices, businesses can greatly reduce the threat of ransomware. A wide-spread attack of this nature should serve as a direct wakeup call to businesses of the importance of using supported software and keeping that software up-to-date. Staying on top of product patching is critical, especially when it comes to Microsoft products given the widespread deployment in businesses. It is especially critical to apply all patches that relate to known vulnerabilities. Organizations that had applied the March critical Microsoft Windows patches were not vulnerable to WannaCry. However, the NSA leaks revealed an alarming number of other vulnerabilities in Microsoft and other products as well. Several of which, like WannaCry, have been disclosed by hackers, thus, increasing the likelihood that such vulnerability will be exploited just like WannaCry.
Aside from good "cyber hygiene" including system patches and updates, employee education, training, and awareness about phishing attacks should be mandatory as ransomware often arrives through a phishing campaign. To supplement such training, we have developed a document to help personnel internalize good security practices, both at work and at home: An Individual's Information Security Checklist.
Proactively creating multiple, secure, and physically separate copies of all servers, applications, and data is one of the most impactful preventative measures that will be vital in the event of an attack. Data must be regularly backed up and secured so that the backups are not connected to the computers and networks they are supporting.
For businesses that do not already have an incident response plan that has been vetted, tested, and deployed, now is the time to test and deploy one.
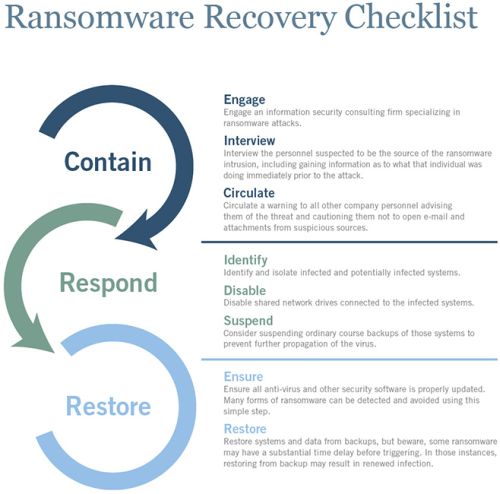
Responding to a Ransomware Attack
While there are a number of preventive steps that a business can take to mitigate the risk of a ransomware attack, there is no such thing as perfect or impenetrable security. Any type of business, whether based in the United States or abroad, is at risk and potentially vulnerable to an attack. No company is completely immune. If an organization finds itself in the unfortunate situation facing a ransomware attack, there are a number of best practices and response measures that can and should be promptly deployed. The steps taken during the initial minutes and hours following the attack are critical and have the ability to greatly reduce the overall impact to the organization, and its ability to recover its systems and data.
Footnote
1. 2017 INTERNET SECURITY THREAT REPORT, Vol. 22 (2017), available for download at https://www.symantec.com/security-center/threat-report
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.











