Guidance note on action items once fraud is detected
An investigation into alleged fraud can expose a company to risks that could result in financial and reputational damage and impact shareholder value. Once fraud is suspected or detected, prompt action is imperative to contain the fall out, address vulnerabilities and take action against perpetrators. Timing is particularly of the essence if reporting requirements (to regulators, law enforcement, customers etc.) are triggered by the fraud. That said, it is also important not to make disclosures without having all the facts at hand, which means the scope and pace of the investigation into the incident of fraud becomes critical. This article provides an SOP to guide actions once fraud is suspected or has been detected to support directors and companies in taking a proactive approach to addressing incidents of fraud.
Step 1: Assessment of risk
When a fraud is reported, and BTG Legal are brought in to conduct a legal investigation into the suspected misconduct, our initial step is to inquire whether the incident that has triggered the investigation is in fact a fraud, and if so, whether that fraud is business critical. We help the client consider and assess the following factors (amongst others) to come to a determination as to whether the incident warrants a full-fledged investigation:
- Is the incident business critical? For instance, does it affect the company business, require disclosures or reporting to regulators etc.?
- Does it involves third party property?
- What is the value of the loss?
- Is other property/business at risk?
- Who is involved - internal employees or only external players? Is it a number of persons or only one or two black sheep?
- What are the system vulnerabilities? Is there a recurring modus operandi or a one-off incident?
If, based on this preliminary assessment, the incident does not appear to constitute fraud, then there may not be the need for a full-fledged investigation. A fact finding exercise may be sufficient, which the company could manage internally.
Step 2: Classification of the threat
As a next step, our primary task is to classify the threat and use this to clearly define the scope of the investigation, with a view to minimize disruptions to the business and employees. For this, we follow the following system of classification:

Step 3: Identify the scope of investigation
Based on the level of the threat, the scope of the investigation will consider:
- Point of origin of risk (if identifiable);
- Point of entry of the risk to the company/property;
- People involved (internal and external) in the fraud;
- Systems affected (internal and external);
- Cut off points to those people and systems (ring fencing);
- Notifications to regulators;
- Notifications to customers;
- Notifications to others – service providers or vendors.
Step 4: Evidence collection
BTG Legal adopts a 2 pronged approach to investigations:
1. Technical evidence: This stage involves gathering and analysing hard evidence (such as tracking the money trail, historic email reviews, invoices, accounting lapses etc.). Some items to keep in mind:
- If equipment (such as handphones, laptops etc.) is confiscated from an employee, keep it secure and unconnected to the network until the specialists commence their investigation.
- Rely on third party specialists if it is required to maintain the legally mandated 'chain of custody' for evidence and avoid subsequent claims of tampering. We often work with IT forensics experts, accounting forensics experts and accountants for information collection and analysis. A third party forensics audit would also hold greater weight than the internal IT audit when seeking relief before courts/LE agencies.
2. Interview evidence: This stage involves interviews and cross examination of suspects (internal and external) based on the hard evidence gathered. Persons potentially involved in the fraud are identified and classified as actors, stakeholders and suspects, based on their suspected level of involvement. BTG Legal designs interviews for each of these suspected players and confronts them with hard evidence collected during the data collection phase during the course of the interview. Some items to keep in mind:
- Use a law firm for interviews or investigations to maintain sanctity of evidence and for privilege and confidentiality purposes. Other non-company representatives (such as from group companies) can be included but will not hold any evidentiary value in any future legal action. Confessions should be recorded as a legally admissible affidavit before witnesses.
- information that some employees or third parties give may be incriminatory or confidential information. Use a law firm to protect such information under privilege if you think it is necessary to do so.
- Create a list of assets affected or targeted (based on information gathered in stage 1) and create images, copies, back-ups and redundancies in case those assets become unavailable (the police usually take them away as evidence).
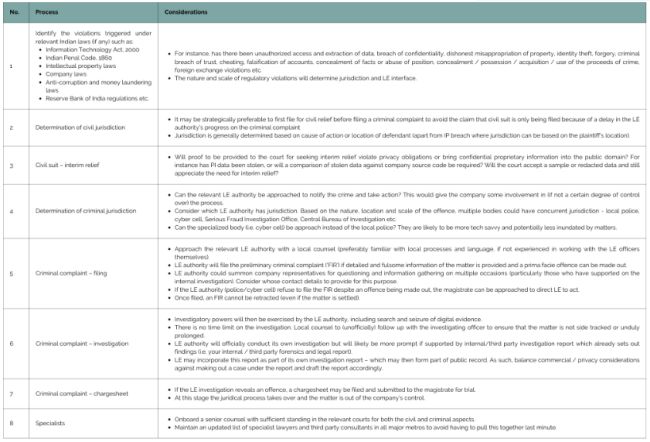
Step 5: Prosecution
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.

