On 30 June 2016, Asset Management Association of China ( "AMAC" ) released the FAQs Regarding Registration and Record-Filing of Private Funds (No. 10) ( "FAQ No. 10" ) under the permission of China Securities Regulatory Commission ( "CSRC" ). FAQ No. 10 allows foreign financial institutions to engage in private securities investment fund management business by establishing foreign-invested enterprises in the People' s Republic of China ( "China" or "PRC" ). A certain number of foreign financial institutions have been actively preparing to launch their wholly foreign-owned private securities investment fund management institutions ( "WFOE PFM" ). For instance, Fidelity and UBS have already completed their WFOEs' registration with AMAC to become WFOE PFMs and commenced their businesses accordingly.
Meanwhile, the impact of the Cybersecurity Law of the People' s Republic of China ( "Cybersecurity Law" , effective as of 1 June 2017) and the subsequently issued or to-be-introduced complementary regulations and guidelines thereunder on the businesses of WFOE PFMs should not be overlooked. Cybersecurity Law applies to any activity in relation to a network operator constructing, operating, maintaining or using the network. It provides the security operation regulations for network operators and requires the classified protection system for cybersecurity, the contingency plans and mechanisms for emergency disposal, the security and protection for the operation of critical information infrastructures ( "CII" ), the security assessment on the cross-border transfer of personal information and important data, etc. The question of how to balance between compliance with Cybersecurity Law and the need of fulfilling the corporate group' s compliance and risk control requirements, and sharing the group' s privileges and resources has become an issue to be considered and resolved by WFOE PFMs.
INVESTMENT AND TRADING MODEL OF WFOE PFMs
FAQ No. 10 requires that a WFOE PFM "shall make investment decisions independently for securities and futures trading it deals with in Mainland China, and shall not place trading orders through any foreign institutions or foreign-based systems, except as otherwise stipulated by CSRC." Unlike a domestically-invested private fund manager, a WFOE PFM should take into consideration the requirement of legal compliance and risk control on a corporate group level in order to comply with both domestic and foreign laws and regulatory requirements, such as those regarding the KYC (know your clients), anti-money laundering, risk control of investment and trading, disclosure of interests. On the other hand, the WFOE PFMs also wish to share the existing advantages and resources of the corporate group (such as researches in securities, quantitative models and risk control systems). Having regard to the concern and needs of a WFOE PFM, the FIX1 model, which applies to WFOE PFMs, is proposed by some foreign institutions.
Specifically, a responsible officer for making investment decisions and a responsible officer for placing trading orders should be equipped with by a WFOE PFM. If FIX model is adopted, a terminal of the global investment management and trading system of the corporate group should be installed in China, and the terminal can connect the PRC securities brokers through the FIX connectivity. After the WFOE PFM' s portfolio manager makes a preliminary investment decision, such decision may be submitted to the global investment management and trading system for compliance and risk control review, and then the final investment decision shall be made by the WFOE PFM' s portfolio manager based on the results of the review. The trader of WFOE PFM places trading orders with the PRC securities brokers through the FIX connectivity (or telephone, e-mail, fax and/or other communication methods), ensuring that the trade routes are transparent and traceable, the trade data is complete and identifiable, the trading process is clear and controllable, and the trade records are all traceable and backed up in China.
The FIX model inevitably involves the storage of investment and trading data outside China and the cross-border transfer of data. Apart from that, in order to satisfy the compliance and risk control requirements on a corporate group level, such as KYC and anti-money laundering, a WFOE PFM has to input the client' s information into the corporate group' s system, which also involves the cross-border transfer of client information.
IMPACT OF CYBERSECURITY LAW ON WFOE PFMs
1. Major Provisions of Cybersecurity Law
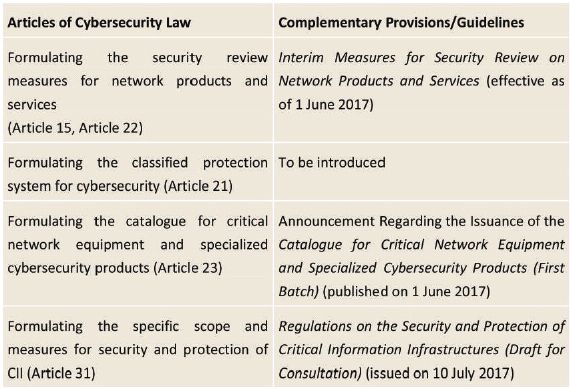
Cybersecurity Law and the Complementary Provisions and Guidelines

Definitions Closely Related to WFOE PFMs under Cybersecurity Law
"Network" refers to the system that is constituted by computers or other information terminals and relevant equipment to collect, save, transmit, exchange, and process information pursuant to certain rules and procedures. The WFOE PFM' s investment management and trading system and other network systems, as well as websites fall into the scope of "Network" .
"Network operators" refer to owners and/or administrators of the network and network service providers. WFOE PFMs, if they own and/or administrate networks, are network operators.
"Critical information infrastructure/CII" refers to critical information infrastructures of important industries and fields, such as public communication and information services, power, transportation, water conservancy, finance, public services, and e-government affairs, as well as other infrastructures that might seriously endanger national security, national economy, people' s livelihood, or public interests in the event of damage, malfunctioning, or data leakage. Emphasized protection is given to CII in addition to the basic classified protection system for cybersecurity.
"Personal information" refers to all kinds of information recorded by electronic methods or otherwise, which can be used independently or in combination with other information to identify a natural person' s identity. Such information includes but is not limited to a natural person' s name, date of birth, ID number, biologically identified personal information, address and telephone number.
"Important data" , with reference to the Measures for the Security Assessment on Cross-border Transfer of Personal Information and Important Data (Draft for Consultation), refers to data closely related to national security, economic development and societal or public interests. The specific scope of "important data" is illustrated in the relevant national standards and the identification guidelines for important data. Appendix A of the Information Security Technology - Guidelines for Data Cross-border Transfer Security Assessment (Draft), a national standard drafted by the National Information Security Standardization Technical Committee, provides the scope of important data.
"Cross-border transfer of data" , with reference to the Measures for the Security Assessment on Cross-border Transfer of Personal Information and Important Data (Draft for Consultation), means the provision of personal information and important data collected or generated in the course of operation in the PRC by network operators to institutions, organizations or individuals located overseas.
Major Content of Cybersecurity Law Applicable to WFOE PFM
- Scope of application: Cybersecurity Law applies to the construction, operation, maintenance and use of network as well as the supervision and administration of cybersecurity within the territory of the PRC. The investment management and trading system used by WFOE PFMs falls under "network" as defined by Cybersecurity Law. Even the server of the global investment management and trading system used by a WFOE PFM under FIX model is located offshore, as the WFOE PFM uses such system within the territory of the PRC, it is our understanding that the usage of the system should be subject to Cybersecurity Law. (Article 2 of Cybersecurity Law)
- Classified protection system for cybersecurity: Cybersecurity Law proposes a "classified protection system for cybersecurity" . Network operators shall fulfill security and protection obligations in accordance with the requirements of the classified protection system for cybersecurity. Such obligations include: formulating internal security management systems and operating instructions, determining the persons responsible for cybersecurity and implementing the cybersecurity and protection responsibilities; taking technical measures to prevent computer viruses, network attacks, network intrusions and other acts endangering cybersecurity; taking technical measures to monitor and record the network operation status and cybersecurity incidents, and preserving web logs for no less than six months pursuant to the provisions; taking measures such as data classification, back-up and encryption of important data, etc. (Article 21 of Cybersecurity Law)
- Network operators shall formulate contingency plans for cybersecurity incidents and carry out such activities as cybersecurity authentication, inspection and risk evaluation. (Articles 25 and 26 of Cybersecurity Law)
- CII: Regulated according to the provisions of Chapter III of Cybersecurity Law on the scope of CII, including but not limited to more stringent security and protection obligations, security review and execution of security confidentiality agreements for purchases of network products and services, onshore storage of personal information and important data collected and generated in the course of operation within the territory of the PRC by CII operators and security assessment where it is necessary to provide such personal information and important data to overseas parties, and annual inspection and assessment. (Articles 31, 34, 35, 36, 37 and 38 of Cybersecurity Law)
- Protection of personal information: To collect and use personal information, network operators shall express the purposes, means and scope of collecting and using the information towards the subject of information, and obtain the consent therefrom. Network operators shall not divulge, distort or damage the personal information collected; and shall not provide the personal information to others without the consent of the persons whose data is collected. The above rules do not apply where the information has been processed and cannot be recovered, which makes it impossible to match such information with specific persons. (Articles 41 and 42 of Cybersecurity Law)
- Legal liability: Chapter VI of Cybersecurity Law clearly provides the legal liabilities of network operators in the event of breach of their relevant responsibilities and obligations, such liabilities include being ordered to effect rectification, being warned, being fined, being ordered to suspend relevant business, stop business for rectification, close down website(s), having the relevant business permits or licenses revoked, having the personnel directly in charge fined, etc.
To read this article in full, please click here.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.


