Cybercrooks target HR departments for the valuable personal details they hold, but there are ways for companies to fight back
The benefits technology can bring to HR are plain to see, even if some of the more recent applications throw up ethical issues. But there is a major obstacle to investment in the area: the cyber threat.
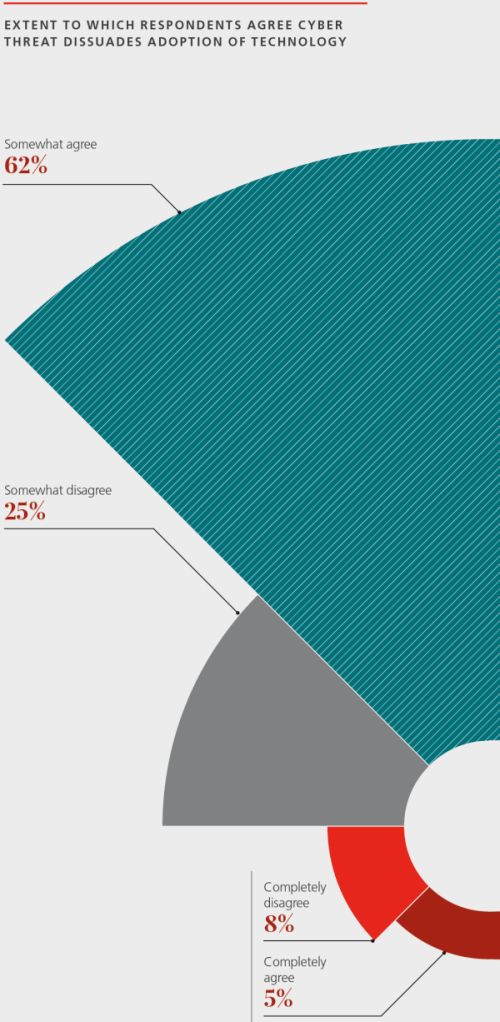
This worry is deterring organisations and HR teams from investing in the technology, according to 67 per cent of respondents to Ius Laboris's forces for change 2020 survey.
"HR is one of the most attractive targets, given the incredible treasure trove of information these departments, and the technology they use, hold," says Professor Daniel Dresner, a cybersecurity expert at Alliance Manchester Business School and the University of Manchester. "HR technology will process information on those wanting to join the company, those already employed and those leaving the business. It's the potential risk of this data getting into the wrong hands that makes the application of HR technology so important."
Max Heinemeyer, director of threat hunting at global cyber artificial intelligence (AI) firm Darktrace, gives the example of a film production studio in America that suffered an attack. "The criminals read through the contact's historical correspondence with an employee at the studio, learnt the typical tone and style of their conversations, and sent a plausible reply to an email from HR," he says. "It was practically indistinguishable from genuine communication, but included a malicious link, plausibly with the motivation of obtaining VIP salary information. These types of attacks are increasingly common and very difficult to detect."
Saryu Nayyar, chief executive of global cybersecurity company Gurucul, points to the data breach suffered by the United States Office of Personnel Management in 2015 as one of the most prominent examples of HR being targeted. "Among the data that was stolen were millions of forms containing personal information gathered in background checks for people seeking government security clearances, along with records of millions of people's fingerprints," she says.
It's the potential risk of this data getting into the wrong hands that makes the application of HR technology so important
The threat from cyberattacks is the same everywhere, but there are cultural differences that can make it more or less likely for people to follow processes, says Yannick Meiller, professor in information management at ESCP Europe Business School, based in France.
"Another element which is different is the national objectives. Every government has agencies around cybercrime, but the way this agency helps private businesses can be different from country to country."
Those working in HR – or using its applications – are particularly vulnerable to a number of threats. Phishing is one of the most common. "This is an engineered attack used to steal user login credentials and details so the attacker can use these to gather sensitive information, such as bank account numbers and credit card information," explains David Keating, VP information technology at CoreHR. A recent example occured in the US city of Tallahassee, when cybercriminals hacked into the city's payroll system and diverted nearly USD 500,000 of staff salaries into their own accounts.
Ransomware is another issue, where criminals effectively lock organisations out of vital systems until a fee has been paid. "A ransomware attack on a payroll company or system would be particularly damaging as many individuals can be immediately impacted and there is very little time to act," says Pali Surdhar, chief security officer at nCipher Security. "Most ransomware attacks are deployed on a Friday, which gives the malware sufficient time to spread."
Then there's the risk that people within organisations or HR teams could compromise data or systems, deliberately or otherwise. Chris Bush, head of security at ObserveIT, gives the example of jailed Morrisons employee Andrew Skelton, who deliberately leaked personal and financial information of 100,000 staff.
The good news is there are a number of measures, both IT- related and wider best practices, that organisations and HR teams can take to help prevent attacks, or ensure they are able to recover and prevent further incidents if the worst should happen.
Review current arrangements
The most important step is to review the company's cybersecurity set-up, including HR technology, says Georg Becker, senior security researcher at the Digital Society Institute, ESMT Berlin. "Depending on such an analysis, upgrading to modern HR technology can actually often have a beneficial effect on the cybersecurity of the company," he says. "Trojan- infested application emails are a good example of how old-school HR technology is by no means inherently more secure than more modern and innovative solutions."
Train staff
Ensuring that all employees are trained in information security awareness is vital, says Professor Meiller; this falls into HR's remit. "The first step is to talk about the importance of information security when you hire a new person," he says. "Then you have to organise regular training and you must be very specific in the seminars you put to people. If you're talking to people in marketing or finance, you should have examples that are very close to them." Training must include the risk of phishing attacks, adds Muttukrishnan Rajarajan, professor of security engineering, at City, University of London, and director of its Institute for Cyber Security. "This is a problem that a lot of organisations face, where people are unaware of the threat and click on links on emails which look very genuine," he warns.
Create clear processes around data
It's vital to ensure that data complies with legislation, including the EU's General Data Protection Regulation (GDPR), but also to be certain that only critical information on employees is kept. "If outsourcing HR technologies, you should research and stay aware of third parties' security practices and maturity, whether they have been involved in a breach before, whether they have a demonstrable focus on security and are compliant with relevant mandates," says Edwin Lemus, vice president of people experience at Alert Logic.
Develop a policy for leavers
HR must ensure that anyone leaving the business does not take data with them. "Adopt protocols that treat data like any other asset which needs to be collected," says Richard Agnew, vice president, Europe, Middle East and Africa at Code42. "The majority of organisations collect laptops, company phones and other hardware, so why should data be treated any differently?"
Consider the limits of technology
For some HR applications, organisations need to check that any changes that have been made are genuine. "Implement email or text-based notifications to employees to alert them when their bank account details change to enable them to spot unauthorised changes quickly," says Will North, chief information security officer at MHR, which provides iTrent HR and payroll software. "For more cautious organisations, as employees changing their bank account details is rarely a monthly or even a yearly task, this functionality could be removed from internet-facing systems and only be available to staff when they are connected to the corporate network."
Work closely with it
HR needs to build strong relationships with IT to help prevent and clean up data breaches. "This will help to identify potential vulnerabilities, establish if new HR tools are secure, and ensure the training in place is up to date and able to tackle the latest risks," says Tristan Liverpool, senior director, systems engineering at F5 Networks. Such collaboration can allow firms to develop and deploy behaviour-based security analytics solutions that can determine normal behaviour for a particular employee or department.
Ultimately, you're trying to show that in a digital world your brand can be relied on Richard Miskella, Joint Managing Partner, Lewis Silkin, Ius Laboris UK
"They can then use this standard behaviour as a baseline to identify risky activities that fall outside the norm and could indicate a cyberattack in progress," says Gurucul's Nayyar.
Challenge vendors
Along with IT, HR needs to challenge software vendors about the level of security in their products. "Software builders must use a secure development life cycle (SDLC), a process in which security is considered at every step of product development, and more and better testing helps flush out vulnerabilities before product release," says Jonathan Knudsen, senior security strategist at Synopsys. "Ask tough questions of vendors, such as 'Tell me about your SDLC' or 'Show me your security testing results'. Second, perform your own security testing on products before making a purchase." This is something that paid off for Erika Lance, senior vice president of people operations at KnowBe4. "One human resource information system we looked into didn't encrypt the information in its system and had a clause that if information was stolen from their site, the customer was the one who was liable," she says. "You have to look closely for that kind of fine print."
Plan for when it happens
It's not a case of if, but when organisations will be hit by some form of cyberattack, warns Richard Miskella, joint managing partner of Lewis Silkin, UK member of Ius Laboris. This means it's important for firms to have plans that enable them to respond. "Putting together the correct teams will take a while, so if you've mapped a real-life scenario and thought about which stakeholders need to be aware of it then you can be much more effective in that first crucial 24 hours," he says. "Ultimately, you're trying to show that in a digital world your brand can be relied on."
Stay vigilant
HR and IT must keep abreast of new trends to ensure they do not get caught out. Mark McClain, chief executive of SailPoint, gives the example of hackers using AI to attack businesses. "A recent study found that when deploying a phishing scheme against humans, it was not the human hacker who had the higher click-through rate, but actually the artificial hacker," he says. "This is just one example of how hackers are bypassing more advanced cybersecurity practices."
Call in the experts
Organisations that have been hacked would do well to bring in specialist help, advises Julian Williams, professor in accounting and finance at Durham University Business School. "Ensure you have some spare capital for this – 1 to 2 per cent of annual turnover – or buy insurance with this built in," he says. "Highly skilled security experts are expensive and for most businesses are not cost effective to retain as staff. My advice is to trust the experts on this."
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.
